华为IPsec VPN基本配置
2022-10-29 和大家一起学路由交换
加入收藏
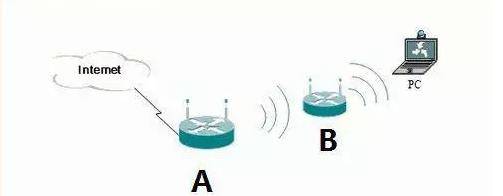
- 实验拓扑

实验拓步
- 环境说明
某企业北京办公区和上海办公区实现京沪FTP_Server数据互通,作为企业网络管理员考虑IT部成本,使用互联网走企业内部数据,保证数据完整性、机密性;需要在北京边缘路由器BJ_AR1和上海边缘路由器SH_AR1之间配置IPsec VPN解决方案,建立IPsec隧道用于某个部门数据互通。
- 配置设备IP
inte.NET路由设备接口地址
[internet]interface g0/0/1
[internet-GigabitEthernet0/0/1]ip address 58.58.58.1 24
[internet]interface g0/0/2
[internet-GigabitEthernet0/0/2]ip address 102.35.35.1 24
[internet]inter LoopBack 0
[internet-LoopBack0]ip address 100.25.25.25 32
BJ_AR1边界路由接口地址
[BJ_AR1]interface g0/0/0
[BJ_AR1-GigabitEthernet0/0/0]ip address 58.58.58.2 24
[BJ_AR1]interface g0/0/1
[BJ_AR1-GigabitEthernet0/0/1]ip address 192.168.1.1 24
[BJ_AR1]interface LoopBack 0
[BJ_AR1-LoopBack0]ip address 10.10.10.10 32
BJ_Core交换机接口地址
Interface IP Address/Mask Physical Protocol
LoopBack0 5.5.5.5/32 up up(s)
MEth0/0/1 unassigned down down
NULL0 unassigned up up(s)
Vlanif1 unassigned up down
Vlanif100 192.168.1.254/24 up up
Vlanif200 192.168.2.254/24 up up
Vlanif300 192.168.3.254/24 up up
Vlanif400 192.168.4.254/24 up up
SH_AR1边界路由接口地址
[SH_AR1]interface g0/0/0
[SH_AR1-GigabitEthernet0/0/0]ip address 102.35.35.2 24
[SH_AR1]interface g0/0/1
[SH_AR1-GigabitEthernet0/0/1]ip address 172.16.30.1 24
[SH_AR1]interface LoopBack 0
[SH_AR1-LoopBack0]ip address 9.9.9.9 32
SH_Core交换机接口地址
Interface IP Address/Mask Physical Protocol
LoopBack0 4.4.4.4/32 up up(s)
MEth0/0/1 unassigned down down
NULL0 unassigned up up(s)
Vlanif1 unassigned up down
Vlanif100 172.16.30.254/24 up up
Vlanif200 172.16.31.254/24 up up
Vlanif300 172.16.32.254/24 up up
Vlanif400 172.16.33.254/24 up up
- 配置OSPF路由协议(实现内网互通)
BJ_AR1路由表(配置步骤略过)
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 16 Routes : 16
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 Static 60 0 RD 58.58.58.1 GigabitEthernet0/0/0
5.5.5.5/32 OSPF 10 1 D 192.168.1.254 GigabitEthernet0/0/1
10.10.10.10/32 Direct 0 0 D 127.0.0.1 LoopBack0
58.58.58.0/24 Direct 0 0 D 58.58.58.2 GigabitEthernet0/0/0
58.58.58.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
58.58.58.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.1.0/24 Direct 0 0 D 192.168.1.1 GigabitEthernet0/0/1
192.168.1.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
192.168.1.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
192.168.2.0/24 OSPF 10 2 D 192.168.1.254 GigabitEthernet0/0/1
192.168.3.0/24 OSPF 10 2 D 192.168.1.254 GigabitEthernet0/0/1
192.168.4.0/24 OSPF 10 2 D 192.168.1.254 GigabitEthernet0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
BJ_Core路由表(配置步骤略过)
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 13 Routes : 13
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 Static 60 0 RD 192.168.1.1 Vlanif100
5.5.5.5/32 Direct 0 0 D 127.0.0.1 LoopBack0
10.10.10.10/32 OSPF 10 1 D 192.168.1.1 Vlanif100
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
192.168.1.0/24 Direct 0 0 D 192.168.1.254 Vlanif100
192.168.1.254/32 Direct 0 0 D 127.0.0.1 Vlanif100
192.168.2.0/24 Direct 0 0 D 192.168.2.254 Vlanif200
192.168.2.254/32 Direct 0 0 D 127.0.0.1 Vlanif200
192.168.3.0/24 Direct 0 0 D 192.168.3.254 Vlanif300
192.168.3.254/32 Direct 0 0 D 127.0.0.1 Vlanif300
192.168.4.0/24 Direct 0 0 D 192.168.4.254 Vlanif400
192.168.4.254/32 Direct 0 0 D 127.0.0.1 Vlanif400
SH_AR1路由表(配置步骤略过)
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 16 Routes : 16
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 Static 60 0 RD 102.35.35.1 GigabitEthernet0/0/0
4.4.4.4/32 OSPF 10 1 D 172.16.30.254 GigabitEthernet0/0/1
9.9.9.9/32 Direct 0 0 D 127.0.0.1 LoopBack0
102.35.35.0/24 Direct 0 0 D 102.35.35.2 GigabitEthernet0/0/0
102.35.35.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
102.35.35.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
172.16.30.0/24 Direct 0 0 D 172.16.30.1 GigabitEthernet0/0/1
172.16.30.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
172.16.30.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
172.16.31.0/24 OSPF 10 2 D 172.16.30.254 GigabitEthernet0/0/1
172.16.32.0/24 OSPF 10 2 D 172.16.30.254 GigabitEthernet0/0/1
172.16.33.0/24 OSPF 10 2 D 172.16.30.254 GigabitEthernet0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
- 配置Easy IP在接口上实用
BJ_AR1边界路由
[BJ_AR1]acl 3000
[BJ_AR1-acl-adv-3000]rule 5 permit ip source 192.168.1.0 0.0.0.255
[BJ_AR1-acl-adv-3000]rule 10 permit ip source 192.168.2.0 0.0.0.255
[BJ_AR1-acl-adv-3000]rule 15 permit ip source 192.168.3.0 0.0.0.255
[BJ_AR1-acl-adv-3000]rule 20 permit ip source 192.168.4.0 0.0.0.255
[BJ_AR1]interface g0/0/0
[BJ_AR1-GigabitEthernet0/0/0]nat outbound 3000
北京PC1可以上外网

北京办公区PC1可以ping通外网
SH_AR1边界路由
[SH_AR1]acl 3000
[SH_AR1-acl-adv-3000]rule 5 permit ip source 172.16.30.0 0.0.0.255
[SH_AR1-acl-adv-3000]rule 10 permit ip source 172.16.31.0 0.0.0.255
[SH_AR1-acl-adv-3000]rule 15 permit ip source 172.16.32.0 0.0.0.255
[SH_AR1-acl-adv-3000]rule 20 permit ip source 172.16.33.0 0.0.0.255
[SH_AR1]interface g0/0/0
[SH_AR1-GigabitEthernet0/0/0]nat outbound 3000
上海PC5可以上外网

上海办公区PC5可以ping通外网
- 配置IPsec VPN
BJ_AR1边界路由
创建高级ACL;定义保护数据流-感兴趣流
[BJ_AR1]acl 3100
[BJ_AR1-acl-adv-3100] rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 172.16.30.0 0.0.0.255
创建IPsec安全提议
[BJ_AR1]ipsec proposal BJ #创建名为BJ的IPsec安全提议
[BJ_AR1-ipsec-proposal-BJ]encapsulation-mode tunnel #定义报文封装模式为隧道模式
[BJ_AR1-ipsec-proposal-BJ]transform esp #定义隧道协议为ESP
[BJ_AR1-ipsec-proposal-BJ]esp authentication-algorithm sha1 #定义认证算法为sha1
[BJ_AR1-ipsec-proposal-BJ]esp encryption-algorithm 3des #定义加密算法为3des
创建IPsec安全策略
[BJ_AR1]ipsec policy P10 10 manual #创建名为P10的IPsec安全策略
[BJ_AR1-ipsec-policy-manual-P10-10]security acl 3100 #引用安全ACL
[BJ_AR1-ipsec-policy-manual-P10-10]proposal BJ #引用安全提议
[BJ_AR1-ipsec-policy-manual-P10-10]tunnel local 58.58.58.2 #本端隧道地址
[BJ_AR1-ipsec-policy-manual-P10-10]tunnel remote 102.35.35.2 #对端隧道地址
[BJ_AR1-ipsec-policy-manual-P10-10]sa spi inbound esp 123456 #定义sa入站参数
[BJ_AR1-ipsec-policy-manual-P10-10]sa string-key inbound esp simple BJSH #定义sa入站密钥
[BJ_AR1-ipsec-policy-manual-P10-10]sa spi outbound esp 654321 #定义sa出站参数
[BJ_AR1-ipsec-policy-manual-P10-10]sa string-key outbound esp simple BJSH #定义sa入站密钥
接口应用IPsec安全策略
[BJ_AR1]interface g0/0/0
[BJ_AR1-GigabitEthernet0/0/0]ipsec policy P1
SH_AR1边界路由
创建高级ACL;定义保护数据流-感兴趣流
[SH_AR1]acl 3100
[SH_AR1-acl-adv-3100] rule 5 permit ip source 172.16.30.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
创建IPsec安全提议
[SH_AR1]ipsec proposal SH #创建名为SH的IPsec安全提议
[SH_AR1-ipsec-proposal-SH]encapsulation-mode tunnel #定义报文封装模式为隧道模式
[SH_AR1-ipsec-proposal-SH]transform esp #定义隧道协议为ESP
[SH_AR1-ipsec-proposal-SH]esp authentication-algorithm sha1 #定义认证算法为sha1
[SH_AR1-ipsec-proposal-SH]esp encryption-algorithm 3des #定义加密算法为3des
创建IPsec安全策略
[SH_AR1]ipsec policy P10 10 manual #创建名为P10的IPsec安全策略
[SH_AR1-ipsec-policy-manual-P10-10]security acl 3100 #引用安全ACL
[SH_AR1-ipsec-policy-manual-P10-10]proposal SH #引用安全提议
[SH_AR1-ipsec-policy-manual-P10-10]tunnel local 102.35.35.2 #本端隧道地址
[SH_AR1-ipsec-policy-manual-P10-10]tunnel remote 58.58.58.2 #对端隧道地址
[SH_AR1-ipsec-policy-manual-P10-10]sa spi inbound esp 654321 #定义sa入站参数
[SH_AR1-ipsec-policy-manual-P10-10]sa string-key inbound esp simple BJSH #定义sa入站密钥
[SH_AR1-ipsec-policy-manual-P10-10]sa spi outbound esp 123456 #定义sa出站参数
[SH_AR1-ipsec-policy-manual-P10-10]sa string-key outbound esp simple BJSH #定义sa入站密钥
接口应用IPsec安全策略
[SH_AR1]interface g0/0/0
[SH_AR1-GigabitEthernet0/0/0]ipsec policy P10
- 配置nat豁免
BJ_AR1边界路由
[BJ_AR1]acl 3000
[BJ_AR1-acl-adv-3000]rule 4 deny ip source 192.168.1.0 0.0.0.255 destination 172.16.30.0 0.0.0.255
SH_AR1边界路由
[SH_AR1]acl 3000
[SH_AR1-acl-adv-3000]rule 4 deny ip source 172.16.30.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
- 实现京沪FTP_Server互通

北京服务器ping上海服务器可以ping通

北京核心交换机ping上海服务器可以ping通

上海服务器ping北京服务器可以ping通

上海核心交换可以登录北京ftp服务器