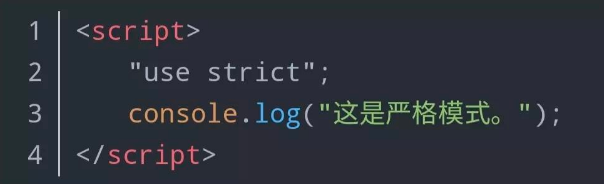
JS请求参数加密破解
源代码如下
```js
function ajax() {
var _0x41e66d = _0xe062, _0x31cef8 = {
'type': arguments[0x0][_0x41e66d(0x91)] || _0x41e66d(0x92),
'url': arguments[0x0][_0x41e66d(0x93)] || '',
'async': arguments[0x0]['async'] || !0x0,
'data': arguments[0x0][_0x41e66d(0x94)] || null,
'headers': arguments[0x0][_0x41e66d(0x95)] || {},
'dataType': arguments[0x0][_0x41e66d(0x96)] || 'text',
'contentType': arguments[0x0][_0x41e66d(0x97)] || 'Application/x-www-form-urlencoded',
'beforeSend': arguments[0x0][_0x41e66d(0x98)] || function () {
},
'success': arguments[0x0][_0x41e66d(0x99)] || function () {
},
'error': arguments[0x0][_0x41e66d(0x9a)] || function () {
_0x31cef8[_0x41e66d(0x98)]();
var _0x1afd14 = createXmlHttpRequest();
_0x1afd14[_0x41e66d(0x9b)] = _0x31cef8[_0x41e66d(0x96)], _0x1afd14[_0x41e66d(0x9c)](_0x31cef8['type'], _0x31cef8['url'], _0x31cef8[_0x41e66d(0x9d)]), _0x1afd14[_0x41e66d(0x9e)]('Content-Type', _0x31cef8['contentType']), Object['keys'](_0x31cef8[_0x41e66d(0x95)])['forEach'](function (_0x49c282) {
var _0x1500ae = _0xe062;
_0x1afd14[_0x1500ae(0x9e)](_0x49c282, _0x31cef8[_0x1500ae(0x95)][_0x49c282]);
}), _0x1afd14[_0x41e66d(0x9f)](convertData(_0x31cef8[_0x41e66d(0x94)])), _0x1afd14[_0x41e66d(0xa0)] = function () {
var _0x46e788 = _0xe062;
0x4 === _0x1afd14[_0x46e788(0xa1)] && (0xc8 === _0x1afd14['status'] ? _0x31cef8[_0x46e788(0x99)](_0x1afd14[_0x46e788(0xa2)]) : _0x31cef8[_0x46e788(0x9a)]());
代码分析思路
1.代码中有大部分的0x标识的字符,如果是在括号内的,并且没有被引号圈起来的,那就是十六进制的。
直接到[**jsjiami.com**](https://www.jsjiami.com/jiemi.html)解密一遍,就可以得到如下代码,看不懂的0x都变成目标字符了。
```js
function ajax() {
var _0x41e66d = _0xe062,
_0x31cef8 = {
'type': arguments[0][_0x41e66d(145)] || _0x41e66d(146),
'url': arguments[0][_0x41e66d(147)] || '',
'async': arguments[0]['async'] || !0,
'data': arguments[0][_0x41e66d(148)] || null,
'headers': arguments[0][_0x41e66d(149)] || {},
'dataType': arguments[0][_0x41e66d(150)] || 'text',
'contentType': arguments[0][_0x41e66d(151)] || 'application/x-www-form-urlencoded',
'beforeSend': arguments[0][_0x41e66d(152)] || function() {},
'success': arguments[0][_0x41e66d(153)] || function() {},
'error': arguments[0][_0x41e66d(154)] || function() {}
_0x31cef8[_0x41e66d(152)]();
var _0x1afd14 = createXmlHttpRequest();
_0x1afd14[_0x41e66d(155)] = _0x31cef8[_0x41e66d(150)], _0x1afd14[_0x41e66d(156)](_0x31cef8['type'], _0x31cef8['url'], _0x31cef8[_0x41e66d(157)]), _0x1afd14[_0x41e66d(158)]('Content-Type', _0x31cef8['contentType']), Object['keys'](_0x31cef8[_0x41e66d(149)])['forEach'](function(_0x49c282) {
var _0x1500ae = _0xe062;
_0x1afd14[_0x1500ae(158)](_0x49c282, _0x31cef8[_0x1500ae(149)][_0x49c282]);
}), _0x1afd14[_0x41e66d(159)](convertData(_0x31cef8[_0x41e66d(148)])), _0x1afd14[_0x41e66d(160)] = function() {
var _0x46e788 = _0xe062;
4 === _0x1afd14[_0x46e788(161)] && (200 === _0x1afd14['status'] ? _0x31cef8[_0x46e788(153)](_0x1afd14[_0x46e788(162)]) : _0x31cef8[_0x46e788(154)]());
3.懂JS的人都知道,arguments是函数的入参函数,虽然这个ajax函数没有定义参数,但是这里可以看到,写代码的作者是把形参利用这个方式传进来了,我们如果想做的美观可以把他提出去。
4.剩下的就是正常解码了。