IPSec热点
2020-10-29
加入收藏
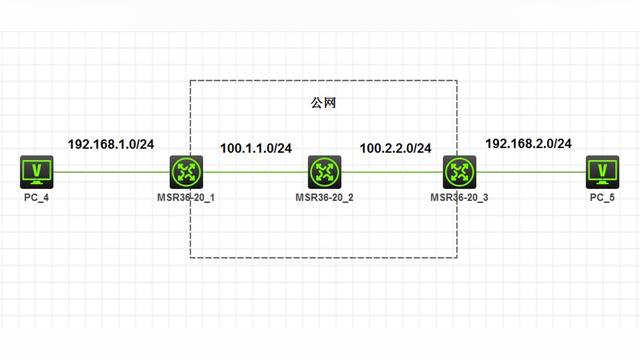
一:GRE-over-IPSec:

【DeviceA】
1.配置IP地址
2.GRE
[DeviceA] interface tunnel 0 mode gre
[DeviceA-Tunnel0] ip address 10.1.1.1 255.255.255.0
[DeviceA-Tunnel0] source 202.115.22.48
[DeviceA-Tunnel0] destination 202.115.24.50
[DeviceA-Tunnel0] quit
3.路由
[DeviceA] ip route-static 192.168.2.1 255.255.255.0 tunnel 0
4.ACL
[DeviceA] acl number 3000
[DeviceA-acl-adv-3000] rule 0 permit gre source 202.115.22.48 0 destination 202.115.24.50
0
[DeviceA-acl-adv-3000] quit
5.IKE+IPSec:
[DeviceA] ike keychain keychain1
[DeviceA-ike-keychain-keychain1] pre-shared-key address 202.115.24.50 255.255.255.0 key
simple 123
[DeviceA-ike-keychain-keychain1] quit
[DeviceA] ike profile profile1
[DeviceA-ike-profile-profile1] keychain keychain1
[DeviceA-ike-profile-profile1] local-identity address 202.115.22.48
[DeviceA-ike-profile-profile1] match remote identity address 202.115.24.50 255.255.255.0
[DeviceA-ike-profile-profile1] quit
[DeviceA] ipsec transform-set tran1
[DeviceA-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceA-ipsec-transform-set-tran1] protocol esp
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm des
[DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceA-ipsec-transform-set-tran1] quit
25
[DeviceA] ipsec policy policy1 1 isakmp
[DeviceA-ipsec-policy-isakmp-policy1-1] security acl 3000
[DeviceA-ipsec-policy-isakmp-policy1-1] remote-address 202.115.24.50
[DeviceA-ipsec-policy-isakmp-policy1-1] transform-set tran1
[DeviceA-ipsec-policy-isakmp-policy1-1] ike-profile profile1
[DeviceA-ipsec-policy-isakmp-policy1-1] quit
6.接口应用
[DeviceA] interface gigabitethernet 2/0/2
[DeviceA-GigabitEthernet2/0/2] ipsec Apply policy policy1
[DeviceA-GigabitEthernet2/0/2] quit
二:IPSec-over-GRE:

【DeviceA】
1.配置IP地址
2.GRE
[DeviceA] interface tunnel 0 mode gre
[DeviceA-Tunnel0] ip address 10.1.1.1 255.255.255.0
[DeviceA-Tunnel0] source 202.115.22.48
[DeviceA-Tunnel0] destination 202.115.24.50
[DeviceA-Tunnel0] quit
3.路由
[DeviceA] ip route-static 192.168.2.1 255.255.255.0 tunnel 0
4.ACL
[DeviceA] acl number 3000
[DeviceA-acl-adv-3000] rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
[DeviceA-acl-adv-3000] quit
5.IKE+IPSec:
[DeviceA] ike keychain keychain1
[DeviceA-ike-keychain-keychain1] pre-shared-key address 10.1.1.2 255.255.255.0 key simple
123
[DeviceA-ike-keychain-keychain1] quit
[DeviceA] ike profile profile1
[DeviceA-ike-profile-profile1] keychain keychain1
[DeviceA-ike-profile-profile1] local-identity address 10.1.1.1
[DeviceA-ike-profile-profile1] match remote identity address 10.1.1.2 255.255.255.0
[DeviceA-ike-profile-profile1] quit
[DeviceA] ipsec transform-set tran1
[DeviceA-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceA-ipsec-transform-set-tran1] protocol esp
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm des
[DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceA-ipsec-transform-set-tran1] quit
25
[DeviceA] ipsec policy policy1 1 isakmp
[DeviceA-ipsec-policy-isakmp-policy1-1] security acl 3000
[DeviceA-ipsec-policy-isakmp-policy1-1] remote-address 10.1.1.2
[DeviceA-ipsec-policy-isakmp-policy1-1] transform-set tran1
[DeviceA-ipsec-policy-isakmp-policy1-1] ike-profile profile1
[DeviceA-ipsec-policy-isakmp-policy1-1] quit
6.接口应用
[DeviceA] interface tunnel 0
[DeviceA-Tunnel0] ipsec apply policy policy1
[DeviceA-Tunnel0] quit