今天粉丝说公司现在有两台服务器,分别是web(server1)和ftp(server2),局域网有两个网段,要求这两个网段不能互访,而且都要访问web服务器,但是不能访问ftp服务器。
需要帮助解决,后来我建议采用acl三层隔离vlan的方法解决。
下面是拓扑图和详细过程。
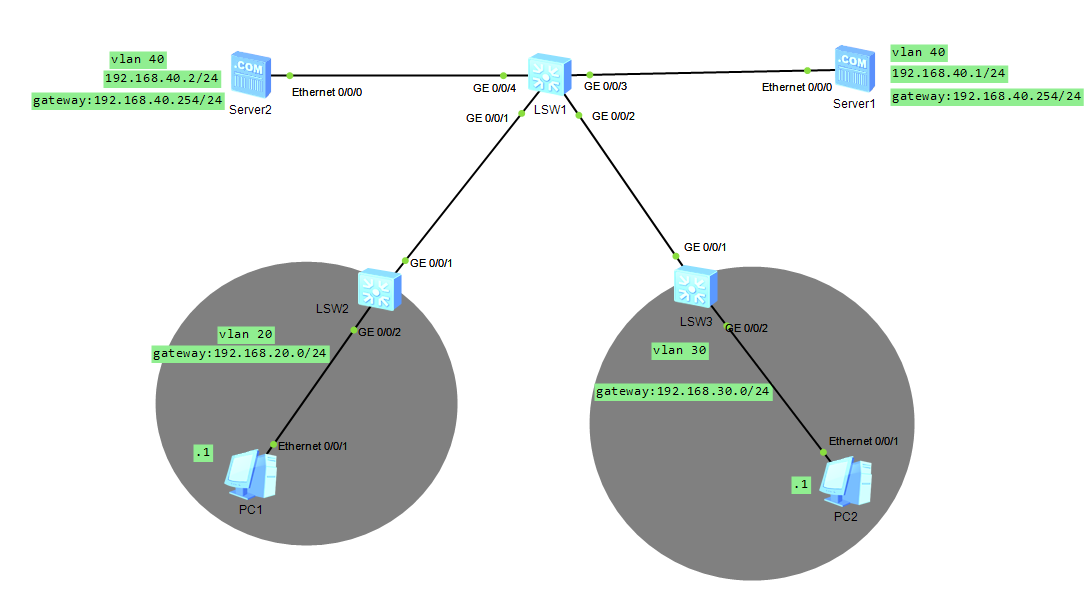
一、基本配置
1.1、PC
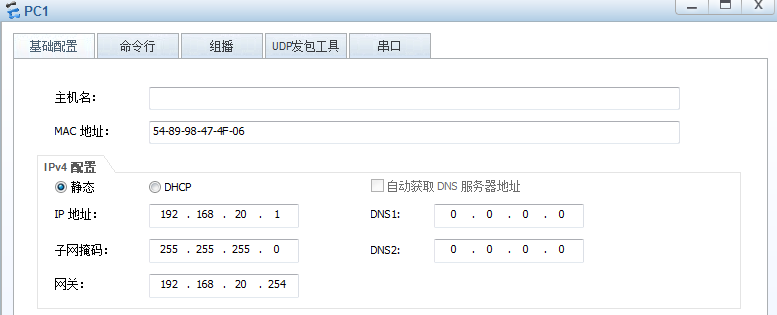
PC1
Ip:192.168.20.1
子网掩码:255.255.255.0
网关:192.168.20.254
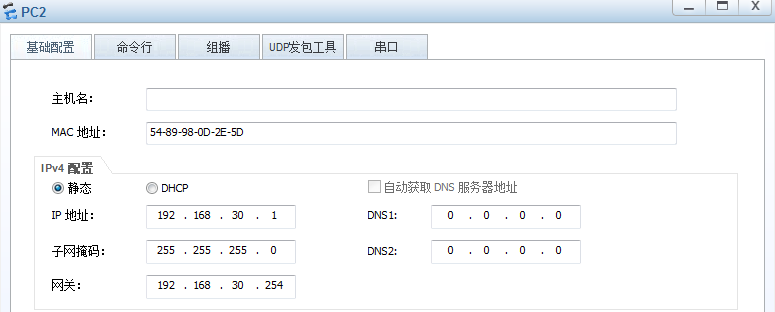
PC2
Ip:192.168.30.1
子网掩码:255.255.255.0
网关:192.168.30.254
1.2、二层交换机
1.2.1、Sw2配置
<Huawei>sys
[Huawei]sys sw2
[sw2]vlan 20
[sw2-vlan20]int g0/0/2
[sw2-GigabitEthernet0/0/2]port link-type access
[sw2-GigabitEthernet0/0/2]port default vlan 20
[sw2]int g0/0/1
[sw2-GigabitEthernet0/0/1]port link-type trunk
[sw2-GigabitEthernet0/0/1]port trunk allow-pass vlan 20
1.2.2、Sw3配置
<Huawei>sys
[Huawei]sys sw3
[sw3]vlan 30
[sw3]int g0/0/2
[sw3-GigabitEthernet0/0/2]p l a
[sw3-GigabitEthernet0/0/2]p d v 30
[sw3]int g0/0/1
[sw3-GigabitEthernet0/0/1]p l t
[sw3-GigabitEthernet0/0/1]p t a v 30
1.3、三层交换机
Sw1配置
<Huawei>sys
[Huawei]sys sw1
[sw1]vlan batch 20 30 40
[sw1]int g0/0/1
[sw1-GigabitEthernet0/0/1]p l t
[sw1-GigabitEthernet0/0/1]p t a v 20
[sw1]int g0/0/2
[sw1-GigabitEthernet0/0/2]p l t
[sw1-GigabitEthernet0/0/2]p t a v 30
[sw1]int g0/0/3
[sw1-GigabitEthernet0/0/3]p l a
[sw1-GigabitEthernet0/0/3]p d v 40
[sw1]int g0/0/4
[sw1-GigabitEthernet0/0/4]p l a
[sw1-GigabitEthernet0/0/4]p d v 40
配置各vlan的网关
[sw1]int vlanif 20
[sw1-Vlanif20]ip addr 192.168.20.254 24
[sw1]int vlanif 30
[sw1-Vlanif30]
[sw1-Vlanif30]ip addr 192.168.30.254 24
[sw1]int vlanif 40
[sw1-Vlanif40]ip addr 192.168.40.254 24
1.4、服务器配置
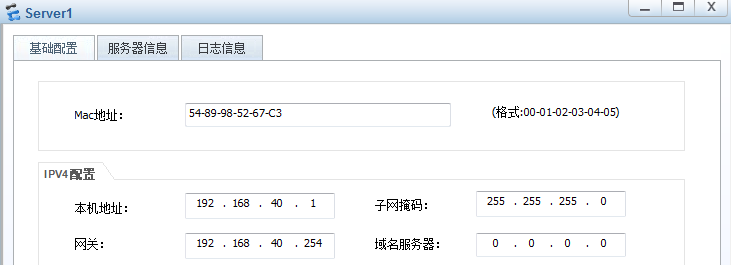
Server1
IP:192.168.40.1
掩码:255.255.255.0
网关:192.168.40.254
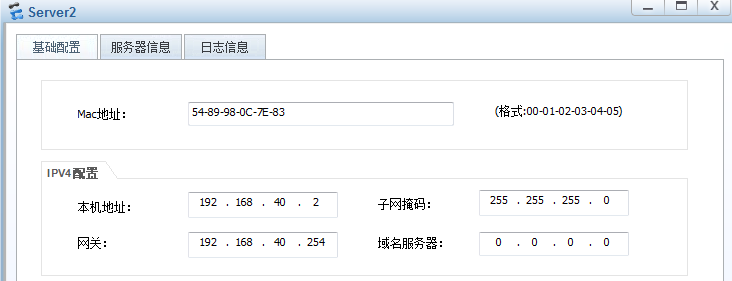
Server2
IP:192.168.40.2
掩码:255.255.255.0
网关:192.168.40.254
1.5、测试
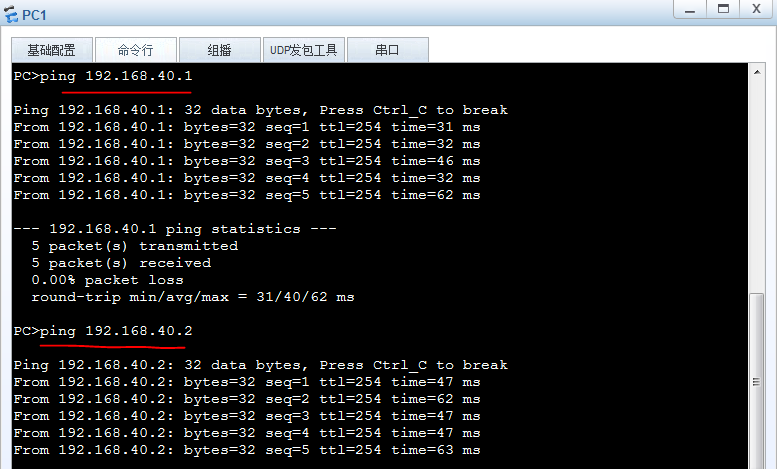
PC1到server1和server2都通。
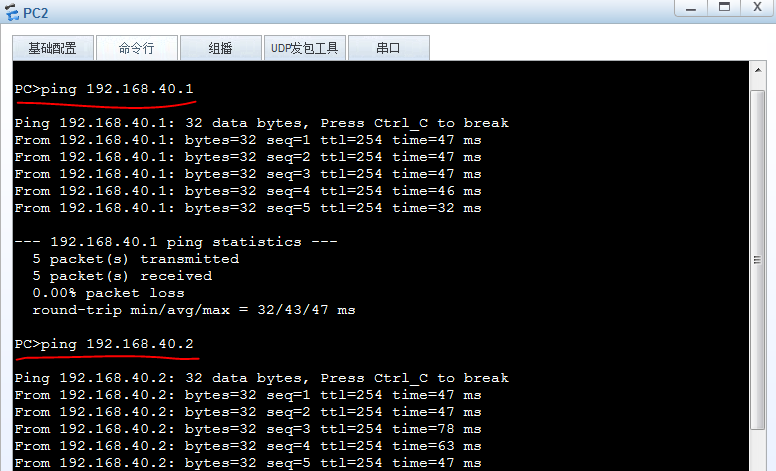
PC2到server1和server2都通。
二、ACL策略配置
2.1、需求
2.1.1、配置acl定义192.168.10.0/24与192.168.20.0/24网段不允许互相访问;
2.2.2、两个网段都可以访问192.168.30.1/24(server1-web),但是不能访问192.168.30.2/24(server2-ftp);
2.2、配置ACL
2.2.1、定义允许的ACL规则
[sw1]acl number 3001
[sw1-acl-adv-3001]rule permit ip source 192.168.20.0 0.0.0.255 destination 192.1
68.40.1 0
[sw1-acl-adv-3001]rule permit ip source 192.168.30.0 0.0.0.255 destination 192.1
68.40.1 0
2.2.2、定义禁止的ACL规则
[sw1]acl number 3002
[sw1-acl-adv-3002]rule deny ip source 192.168.20.0 0.0.0.255 destination 192.168
.30.0 0.0.0.255
[sw1-acl-adv-3002]rule deny ip source 192.138.30.0 0.0.0.255 destination 192.168
.20.0 0.0.0.255
[sw1-acl-adv-3002]rule deny ip source 192.168.20.0 0.0.0.255 destination 192.168
.40.2 0
[sw1-acl-adv-3002]rule deny ip source 192.168.30.0 0.0.0.255 destination 192.168
.40.2 0
2.2.3、定义流分类
[sw1]traffic classifier tc1 operator and
[sw1-classifier-tc1]if-match acl 3001
[sw1]traffic classifier tc2 operator and
[sw1-classifier-tc2]if-match acl 3002
2.2.4、定义流行为,这里才是真正决定是允许还是禁止
[sw1]traffic behavior tb1
[sw1-behavior-tc1]permit
[sw1]traffic behavior tb2
[sw1-behavior-tc2]deny
2.2.5、定义流策略 (这里最好注意顺序,避免一些问题发生)
[sw1]traffic policy tp
[sw1-trafficpolicy-tp]classifier tc1 behavior tb1
[sw1-trafficpolicy-tp]classifier tc2 behavior tb2
2.2.6、靠近源地址端接口(下行)入方向下发
[sw1]vlan 20
[sw1-vlan20]traffic-policy tp inbound
[sw1-vlan20]vlan 30
[sw1-vlan30]traffic-policy tp inbound
2.3、测试
PC1到server1通,到server2不通
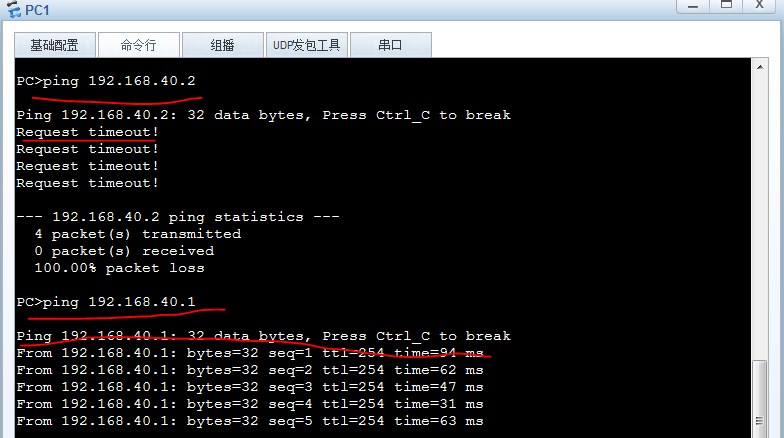
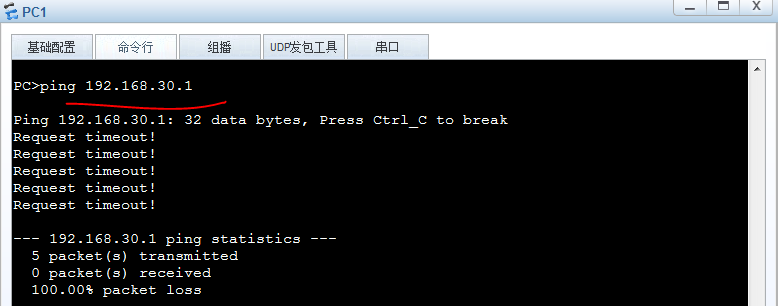
PC1到PC2 不通
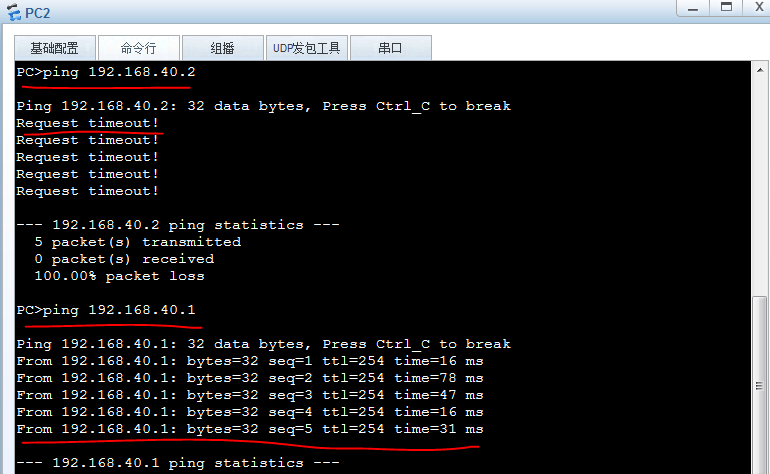
PC2到server2不通,到server1通
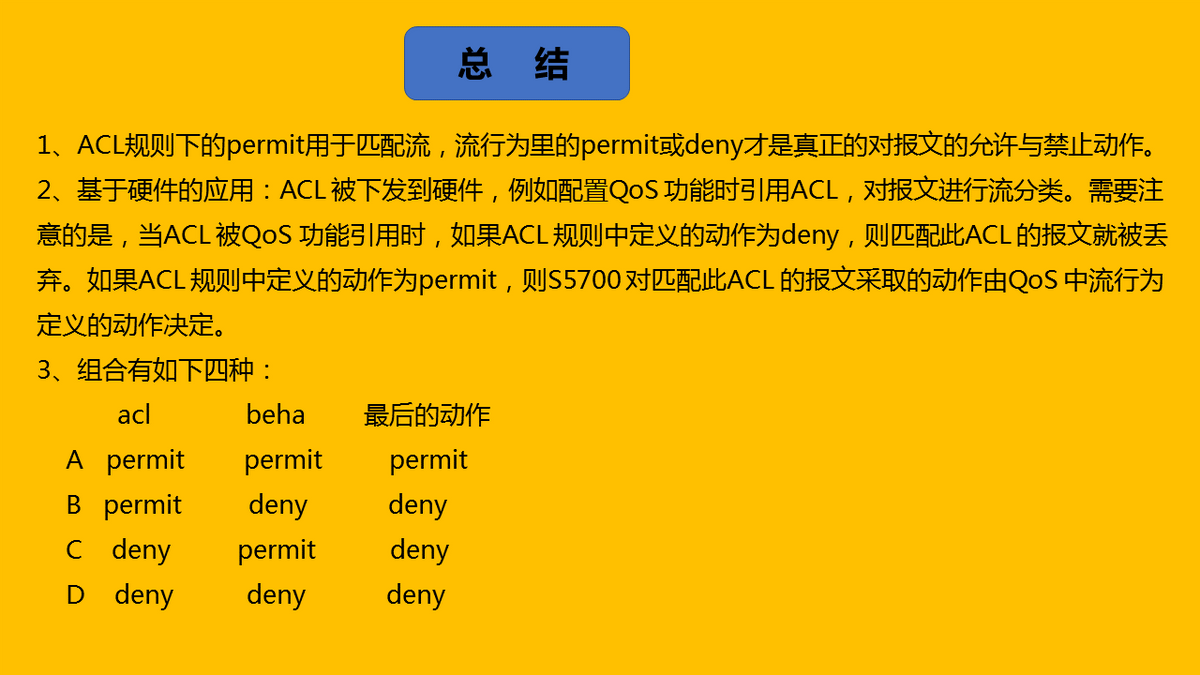
三、说明:

四、总结